Updated February 2, 2005
From time to time, it is not possible to remove spyware with standard anti-spyware tools. Some spyware programs directly attack programs like Adaware and Spybot Search and Destroy, and prevent them from working. Other times, spyware programs are simply impossible for current anti-parasite software to remove. Regardless, there are circumstances in which someone might have to remove spyware manually.
When dealing with Spyware any spyware a good place to start is to identify the threat. Often, ones first clue will be a message from Adaware or some similar tool that a spyware program is present on a computer, but cannot be removed. Other times, a mysterious process will appear in a Hijack This scan. In a worse scenario, unpleasant or undesirable behaviors continue even after a thorough spyware cleaning.
Identifying Spyware
The simple case in identifying spyware is direct information from your Anti-Spyware (AS) programs. In this case, youll be given the common name of the spyware or the company that made it. For example, Spybot Search and Destroy might tell you that your computer is infected with a parasite program called C2. This very basic information is actually enough to start an investigation into the root of spyware problems.
Another possible option in spyware detection is seeing an unusual process in the Windows Task Manager Process View. You can start Task Manage by typing CTRL-ALT-DEL, or by right clicking on your Windows Taskbar and choosing Task Manager. The Process view is the second tab from the left.
 In
this case,
the Task Manager is showing a number of non-standard programs running
on my
computer. I might be curious about LexBceS.exe or CLI.exe or
btdownloadgui.exe.
In
this case,
the Task Manager is showing a number of non-standard programs running
on my
computer. I might be curious about LexBceS.exe or CLI.exe or
btdownloadgui.exe.
Of course, one has to be
familiar with the normal contents of
this Window, and what the normal
running programs do, before any judgement of what
should or shouldnt be there can be made. Clearly, there is work here
that
needs to be done.
Task Manager is actually a sub-optimal tool. It turns out that, by
design, it
does not show every program running
on a computer. Spyware programmers know of this deficiency, and many
spyware
programs can hide from Task Manager. For this reason, a very useful
tool for
spyware hunters is Process Explorer from sysinternals.com. Process
Explorer
does a much better job of showing running programs, as well as
indicating what
files on a computer are being used by those programs.
Most people downloading Process Explorer will wanted the 32-bit version
for
Windows 2000/XP/Server 2003.

Process Explorer goes into somewhat more detail about the programs running on a computer. In this case, we can see that LexBceS.exe came from Lexmark, a company that makes printers. We can also see a list of files and registry entries associated with that program. This is exactly the sort of information one might need to know to take spyware off a computer!
Of course, in all likelihood, Process Explorer wont be something to look at until a problem is already evident. A more common tool, one that should already be in a good spyware-hunters arsenal, is Hijack This. The original intention of Hijack This was to consolidate the view of a number of different places on a Windows computer that spyware will typically attack. Some spyware programs make changes to Internet Explorer startup or default elements such as the start or search page. Other programs add elements of themselves to the lists of Windows startup programs. Still others become Browser Help Objects(BHOs), which in some way change basic functionality within Internet Explorer.
Hijack This
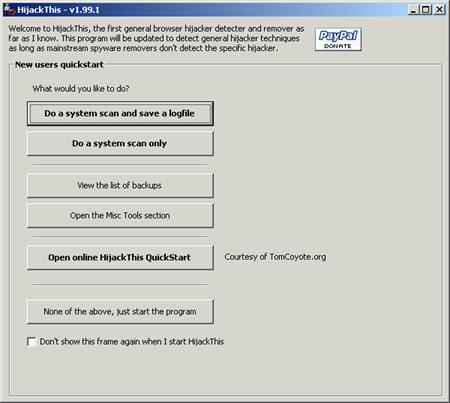
Hijack This is available from Merijn.org. This is what the program looks like when it starts up. Hijack This is a tool more for technicians and users not afraid to do a little research. Because it is such a powerful tool, and one so capable of potentially damaging a computer, it has several different startup modes. The simplest way to use it is the default: Do a system scan and save a logfile. In this case, a plain-text log is created that can be emailed to a more knowledgeable technician or posted on an internet forum. Hijack This, like other Anti-Spyware tools, is most effective when run in Safe Mode.
Users can also Do a System Scan Only, which gives readout of information Hijack This normally shows, without the ability to make changes.
Hijack This includes several very powerful tools besides its basic spyware-removing functionality. These tools are available in the Misc Tools section but are beyond the scope of this document.
The online QuickStart is a simple web page with a brief Hijack This tutorial.
Finally, None of the above, just start the program is the standard means to actually use Hijack This. This is the option that spyware-hunters will normally want.
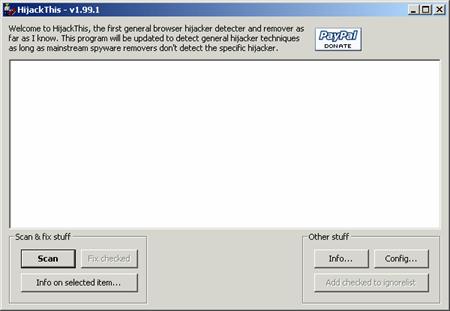 And
this is
what Hijack This looks like when it starts. Not a
whole lot to do yet. We have to click the Scan button to make anything
happen.
And
this is
what Hijack This looks like when it starts. Not a
whole lot to do yet. We have to click the Scan button to make anything
happen.
Hijack This actually scans for any behavior that is different from the default Windows configuration, as related to Start Up and Internet Explorer. Because of this, almost everyone will have something unusual detected when Hijack This scans are run. Unlike other anti-spyware programs, just because something is detected by Hijack This does not mean it is not a legitimate change.

Once Hijack This has run its scan, the results are displayed and are categorized according to the type of possible threat.
In the example here, we can see O4, O8, O9, O12, O16 and O20 changes. Clicking the Info on Selected Item button will explain the threat category in more detail. For example, an O16 threat describes an ActiveX program that has been downloaded and run by Internet Explorer. The O16-type threats visible in this scan, however, are both legitimate; one is from Housecall.Antivirus.Com, the other is from Microsoft's Technical Download service.
 The
explanations of the various threats Hijack This can
detect really are friendly and mostly non-technical.
The
explanations of the various threats Hijack This can
detect really are friendly and mostly non-technical.
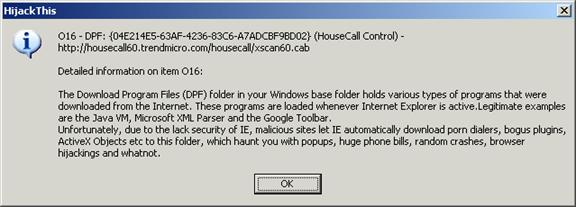
To remove any of the things that Hijack This has detected, simply check the box next to that line, then click the Fix Checked button. 99% of the time, if Hijack This is being run from safe mode, the item or items you have objected to will be removed forever.
In the event that you later learn that you have mistakenly removed something you do, in fact, need, Hijack This also makes a folder called Backups that contain everything needed to restore whatever it removed in the past. Items can be restored on a singular basis.
Of course, sometimes it is possible to easily identify something that needs to be removed from your computer after a Hijack This scan. Something like freepokerservice.exe probably doesnt belong, but what about the things on that list youve never heard of? If youre a first time user, practically everything is going to be something you havent heard of. But what do you do with ijlysseb.exe?
The correct answer is get on the internet and do some research.
Research
In all honesty, researching what the programs running, or the programs starting, or the things that have already been detected by anti-spyware programs is a lot easier if you can do it on another computer while youre looking at the one youre trying to clean. Its not absolutely essential, but switching between normal mode for internet access and safe mode for spyware removal gets really old really fast.
An internet connection is essential for this work. Do what you have to do to get one. Hopefully, using Firefox or some other non-IE browser will minimize the annoyance if youre forced to use a computer that still has spyware.
So where to start?
Google.
Want to find out what the heck ijlysseb.exe is? Type it in Google's search box and find out. The very first search result has this to say:
Lop, which stands for Live
Online Portal, is a browser hijacker that resets the start and search
pages in
IE. (Its aliases include: C2; Lop C2Media; Lop.com; Tubmo;
Ultimate Browser Enhancer; as well as Lop/Active and variants such as
Lop/Dialer, Lop/IMZ, and Lop/Trinity.) Lop variants also may install an
Accessories toolbar in IE, add shortcuts to the Favorites menu, monitor
online
activity, install a porn dialer, and load other spyware and third-party
programs onto the system.
Hm. Porn Dialer? Load Other Spyware? Monitor Online Activity? Its probably safe to say that ijlysseb.exe isnt our friend.
But what about something that should be on your computer? Try a Google search for svchost.exe.
Again, the very first search result will paint a very clear picture:
svchost.exe is a system process belonging to the Microsoft Windows Operating System which handles processes executed from DLLs. This program is important for the stable and secure running of your computer and should not be terminated.
That one should probably stay. J
Over the course of doing these searches, a small number of web sites are going to keep showing up again and again near the top of the search results page. These sites tend to be major and important sources for information about the programs running on a computer, and about spyware in particular. If one or more of them comes up in your query about a particular program, its probably a good place to look for information.
Some of the most useful sites for information about spyware are:
- Doxdesk.com in addition to listing information about various malware programs, doxdesk also has information about spyware removal programs, including purposefully malicious anti-spyware software.
- Castlecops.com This web site might as well be called The Place to figure out what to do with Hijack This. In the blue frame down the left-hand side of the Castlecops page are dozens of tools for finding out what startup programs do, what registry entries do what, and what those mysterious names on your Task Manager/Process Explorer list are. Castlecops uses the same naming system as Hijack This, so if youre curious about what a particular O20 threat might be, Castlecops is the place to go.
- SpywareWarrior.com This site serves as an aggregation point for breaking news about Spyware. New spyware is found every single day; sometimes, SpywareWarrior is the only site that will have information about your particular problem.